Inside the Surge of Social Engineering Attacks in Hospitality
Highlights
*Social engineering threats are rising, with attacks accounting for 25% of hospitality incidents.
*Breaches at MGM Resorts International and Caesars Entertainment highlight the growing attack surface.
*Hoteliers must mount a proactive, multi-layered defense to safeguard operations.
Introduction
Social engineering accounts for 68% of all data breaches, making it one of the top threats to organisations globally.
However, in the aftermath of the multimillion-dollar breaches at MGM Resorts International and Caesars Entertainment, hospitality is now seeing a sharp rise in attacks that use psychology rather than traditional hacking to steal and extort data.
This week’s feature of the VENZA Echo kicks off a three-part series dedicated to the growing social engineering threat facing hoteliers.
Throughout the series, we’ll break down the basics of social engineering, explore the most pressing threats hoteliers are facing today, and outline the defense strategies needed to combat them, diving into the biggest challenges hotels encounter when trying to implement these protections.
What is Social Engineering?
Social engineering is a set of techniques used by criminals to manipulate individuals into revealing confidential information and granting unauthorized access to systems. Instead of directly hacking a network, attackers exploit human psychology, creating a sense of urgency or trust to lull the victim into performing the desired action.
These attacks are driven mostly by financial gain, either through outright data theft or using ransomware to hold information hostage for a payout.
Social engineering attacks come in various forms and are often combined to create more convincing and effective schemes.
The most common forms are:
*Phishing: Fraudulent emails disguised as legitimate ones, aiming to steal data or spread malware through malicious links. This is the most common social engineering tactic globally, with 91% of cyberattacks beginning with a scam email.
*Pretexting: Fabricated scenarios created by attackers to gain a victim’s trust and manipulate them into taking specific actions. This often involves impersonating company executives or vendors, like IT providers, and prompting employees with urgent requests for money or login credentials.
*Vishing: Phone-based phishing, often paired with pretexting. By speaking directly to their victims, attackers can bolster more trust and authority.
*Baiting: Infected USB drives or devices left in public spaces to have an unsuspecting victim plug it in and compromise their system.
Growing Threat
Hospitality is a prime target for social engineering attacks. High employee turnover, 24/7 operations, and a “guest service” mindset make staff more likely to accommodate attackers posing as trusted figures. Add the large amount of sensitive data hotels handle daily, and it’s often an ideal setup for these types of exploits.
However, prior to 2023, most cyberattacks in the hospitality industry were driven by system intrusions—complex attacks involving malware or hacking to achieve their goals.
Now, recent data shows social engineering accounts for 25% of incidents in hospitality, with pretexting doubling over the past year to make up 20% of cases.
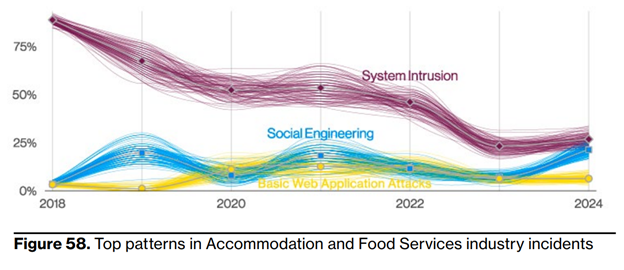
To highlight the growing and dangerous trend, three major cyberattacks shook hospitality within just one month in the fall of 2023—two of which were directly linked to employees falling victim to social engineering tactics.
MGM Resorts and Caesars Entertainment
In August and September 2023, MGM Resorts International and Caesars Entertainment both fell victim to multimillion-dollar ransomware attacks orchestrated by the sophisticated hacker group Scattered Spider. The attacks used similar vishing and pretexting tactics to manipulate employees into granting access to critical systems, leading to severe financial and operational disruptions across both companies.
Hackers targeted MGM Resorts by calling its IT help desk and successfully impersonating an employee using information they gathered from LinkedIn. After a short call, they gained access to a super administrator account with privileges across all MGM’s systems. This allowed them to deploy ransomware and disrupt operations at all 31 properties, including slot machines, reservation systems, and digital keys. The attack cost MGM around $8 million USD per day, with total financial losses estimated at $100 million USD, not including pending or future litigation.
Similarly, Caesars Entertainment suffered a massive data breach through a social engineering attack on an outsourced IT vendor. Hackers used pretexting to access their systems and steal sensitive data from the customer loyalty program. To prevent the release of this data, Caesars reportedly paid a ransom of around $15 million USD.
Defense
To combat the increasing sophistication and scale of social engineering attacks in all its forms, hoteliers should adopt a proactive, multi-layered security strategy.
This approach should include:
*Staff Training and Awareness: Regularly train staff on common social engineering tactics like phishing and pretexting, with role-specific training to cover vulnerabilities specific to different departments. Use simulated phishing and vishing attacks to improve awareness and identify susceptible employees for remediation.
*Policies and Procedures: Implement strict verification protocols for sharing sensitive information, particularly with for third party providers. Establish clear reporting procedures for suspicious behavior.
*Access Control: Enforce role-based access controls so employees only have access to data necessary for their jobs. Perform regular audits to prevent unauthorized access to limit exposure if an attack is successful.
*Secure Communications: Secure internal communications with encryption and require a second channel of verification for sensitive requests. This minimizes the chances of successful impersonation or unauthorized access.
*MFA: Implement Multi-Factor Authentication (MFA) across all systems to strengthen security by requiring employees to provide a second form of verification, such as a text message code or app-based authentication, in addition to their password.
*Incident Response: Develop a comprehensive, well-documented incident response plan that can be quickly activated in the event of a breach. Regularly conduct incident simulations to ensure key personnel are familiar with the procedures and can respond effectively.
Conclusion
As the recent multimillion-dollar breaches at MGM Resorts and Caesars Entertainment have shown, social engineering attacks are rapidly evolving and posing a significant threat to hoteliers. In this first installment of our three-part series on social engineering in hospitality, we’ve introduced the basics of these attacks and the necessary strategies for protection.
Stay tuned for the next two articles in this VENZA Echo series, where we’ll explore the most pressing social engineering threats hotels face today and provide actionable insights on how to tackle the unique challenges of implementing defenses against them.
Feeling overwhelmed? Don’t worry. As the leading experts in hospitality data protection, VENZA offers tailored training and simulated social engineering attacks to assess and strengthen your defenses, providing 360-degree protection for your hotel.
Ready to get started? Contact Sales to discuss signing up for our programs or adding new solutions to your contract.
***
Take VENZA’s free Phishing Test to assess gaps in your human firewall today!

Training your personnel to recognize and report phishing attempts is essential to protecting your guests and their data. Get started by determining your risk and readiness level using this free tool.
***
Want to stay informed? Subscribe to the free VENZA Echo now. You’ll receive a monthly digest with the highlights of our weekly article series and important product updates and news from VENZA.
